OpenClaw's Anthropic API key errors stop your AI assistant completely—messages go unanswered, and your gateway logs fill with authentication failures. The fastest fix for most users is running openclaw doctor --fix for automatic repair. If that doesn't work, use openclaw status --all to get a complete diagnostic report that identifies exactly which authentication component has failed. This guide covers every Anthropic-specific authentication error you'll encounter, from invalid API keys to expired OAuth tokens to the often-misunderstood cooldown mechanism.
TL;DR
Before diving into details, here's what you need to know: Anthropic API key errors in OpenClaw typically stem from three causes—invalid key format (keys must start with sk-ant-api03-), expired OAuth tokens (if using Claude subscription credentials), or environment variable conflicts (leftover ANTHROPIC_BASE_URL or ANTHROPIC_AUTH_TOKEN from previous setups). Run openclaw status --all first to identify your specific issue. The quickest fix is re-running openclaw onboard and selecting Anthropic authentication. For cooldown-related blocks, restart your gateway or wait for the cooldown period to expire.
Quick Diagnosis - Find Your Problem in 5 Minutes
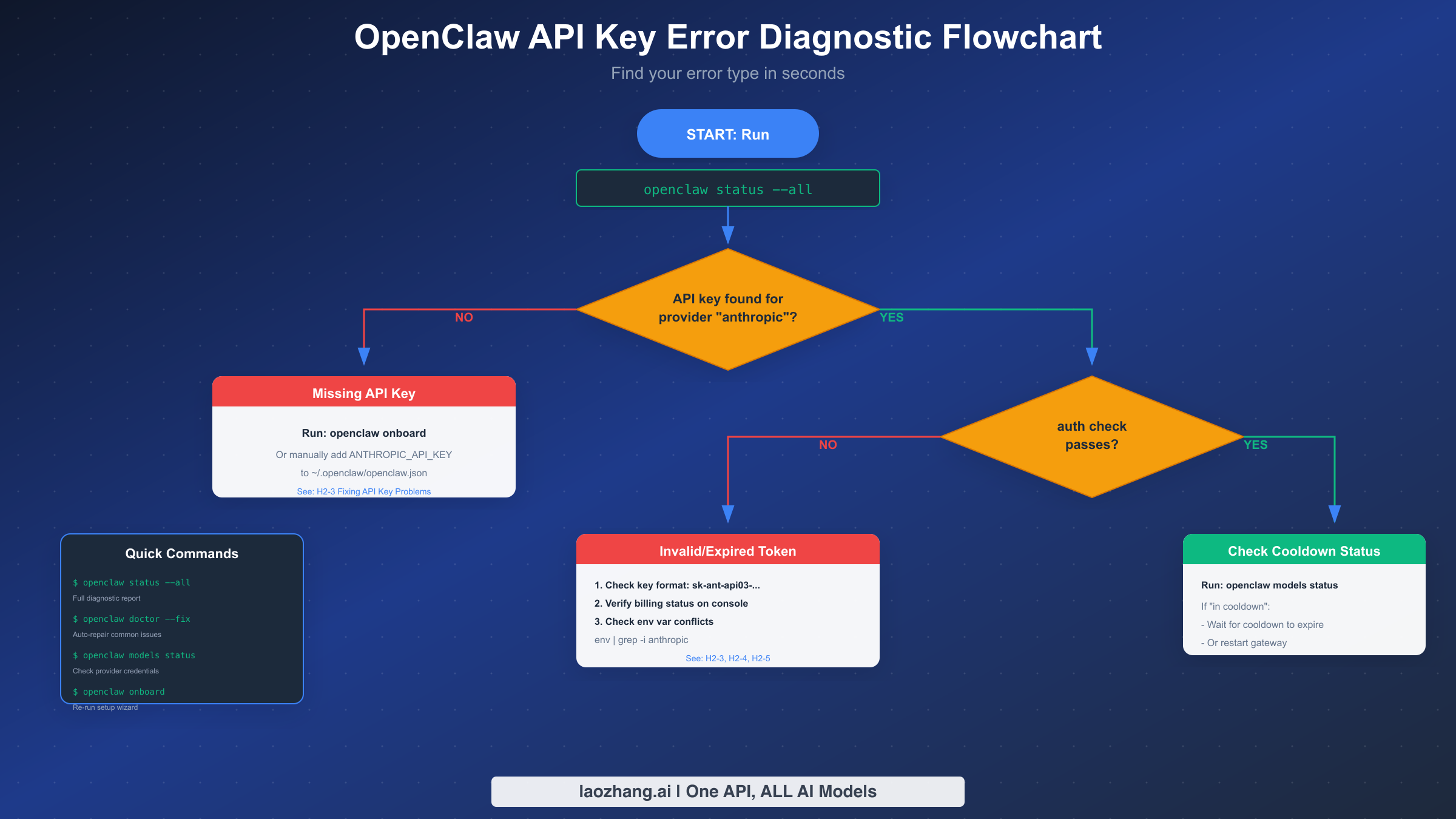
When your OpenClaw agent stops responding to messages, the first step is always diagnosis before attempting any fix. Running the wrong solution for the wrong problem wastes time and can create new issues. OpenClaw provides several diagnostic commands that give you precise information about your authentication state.
The most comprehensive diagnostic is openclaw status --all. This command produces a complete, token-safe report of your current configuration state. The output includes your provider configuration, credential status, and any error messages that have occurred. Copy this output when seeking help—it contains all the information someone needs to diagnose your issue without exposing sensitive credentials.
For a quicker check focused specifically on model authentication, use openclaw models status. This command verifies credentials for each configured provider and reports which ones are working and which have problems. You'll see clear indicators like "valid" or "invalid bearer token" or "no auth configured" for each provider.
If you want automated repair, openclaw doctor --fix attempts to identify and fix common configuration issues automatically. This command checks for syntax errors in configuration files, missing required fields, and obvious misconfigurations. It won't fix credential problems (it can't generate new API keys for you), but it handles many structural issues.
The diagnostic commands reveal specific error patterns. Look for these key indicators in your output: "No API key found for provider 'anthropic'" means credentials are completely missing. "authentication_error: Invalid bearer token" indicates the key exists but is invalid or expired. "all in cooldown" means the provider has been temporarily blocked due to repeated failures.
Identifying Your Error Type
Understanding which error you're facing determines the correct solution path. OpenClaw's Anthropic integration can fail in several distinct ways, each requiring different fixes. The error messages themselves point to the underlying cause.
Authentication errors from Anthropic's API follow a predictable pattern. A 401 error with type "authentication_error" indicates problems with your API key—either the key is invalid, expired, or incorrectly formatted. A 403 error with type "permission_error" means your key is valid but lacks permission for the resource you're trying to access, typically because your account doesn't have the required tier or the key was created with restricted permissions.
The "No API key found for provider 'anthropic'" message appears when OpenClaw's credential store contains no Anthropic credentials at all. This happens with new installations that skipped the authentication step, or when creating new agents that don't inherit credentials from the main agent. The fix is simply providing credentials through one of the supported authentication methods.
OAuth token problems manifest as "OAuth token refresh failed" messages. When using Claude subscription credentials (rather than a direct API key), OpenClaw stores OAuth tokens that need periodic refresh. If the refresh fails—due to network issues, changed password, or revoked access—you'll see this error. The token still exists in your credential store, but it's no longer valid.
Cooldown-related messages like "No available auth profile for anthropic (all in cooldown)" indicate a different problem entirely. Your credentials might be perfectly valid, but OpenClaw has temporarily blocked the provider due to recent failures. This is a protective mechanism, not a credential problem.
For a related but different error, see our guide on troubleshooting the invalid beta flag error, which occurs when using AWS Bedrock or Vertex AI as your Claude provider.
Fixing Invalid API Key Errors
API key problems are the most common Anthropic authentication errors in OpenClaw. The fix depends on whether your key is missing, malformed, or simply invalid.
First, verify your API key format. Anthropic API keys follow a specific pattern—they start with sk-ant-api03- followed by a long alphanumeric string. If your key doesn't match this pattern, it's either not an Anthropic key or has been corrupted during copy-paste. Check for extra spaces, missing characters, or encoding issues. The complete key should be a single continuous string with no whitespace.
To check your current API key configuration, examine your OpenClaw configuration file at ~/.openclaw/openclaw.json. The key should appear under the env section with the ANTHROPIC_API_KEY field. If it's missing or empty, you need to add it.
The recommended method for adding or updating your API key is through the setup wizard. Run openclaw onboard and follow the prompts to configure Anthropic authentication. The wizard validates your key and stores it in the correct location. This method also handles any related configuration that needs to accompany the key.
For manual configuration, edit ~/.openclaw/openclaw.json directly:
json{ "env": { "ANTHROPIC_API_KEY": "sk-ant-api03-your-key-here" }, "agents": { "defaults": { "model": { "primary": "anthropic/claude-sonnet-4" } } } }
Note the model format: direct Anthropic configuration uses anthropic/<model-name> without any prefix like openrouter/. Using the wrong format causes routing errors that look like authentication failures.
After updating your configuration, restart the OpenClaw gateway to apply changes. For Docker deployments, use docker compose restart openclaw-gateway. For systemd services, use systemctl restart openclaw-gateway. Verify the fix by running openclaw models status to confirm credentials are now valid.
If you need to obtain a new Anthropic API key, log into the Anthropic Console at console.anthropic.com, navigate to API Keys, and generate a new key. Remember that Anthropic requires active billing—even if you have free credits, a payment method must be on file before API access works.
Fixing OAuth Token Problems
OAuth token authentication works differently from API keys. Instead of a static credential, OAuth uses tokens that expire and refresh automatically. When the refresh mechanism fails, your authentication breaks even though nothing changed in your configuration.
The most reliable fix for OAuth token problems is switching to a direct API key. OAuth was convenient for users who wanted to reuse their Claude subscription credentials, but the refresh failures make it less reliable for production deployments. If you can obtain an API key, doing so eliminates the entire category of OAuth-related problems.
If you prefer to stay with OAuth, you can manually refresh your tokens. First, understand where OpenClaw stores OAuth credentials: the main location is ~/.openclaw/credentials/oauth.json. For per-agent credentials, check ~/.openclaw/agents/<agentId>/agent/auth-profiles.json.
To refresh OAuth credentials, run openclaw models auth paste-token --provider anthropic. This command prompts you to authenticate again and stores fresh tokens. For headless servers, you'll need to complete the OAuth flow on a machine with a browser, then copy the resulting oauth.json file to your server.
The setup-token approach offers a middle ground. Run openclaw models auth setup-token --provider anthropic to generate a short-lived setup token specifically for initial configuration. This method works well for CI/CD pipelines where you need automated credential provisioning but don't want long-lived secrets in your pipeline configuration.
Watch for environment variables that might interfere with OAuth. If you've previously worked with the Anthropic API directly, you might have ANTHROPIC_AUTH_TOKEN or ANTHROPIC_BASE_URL set in your environment. These variables override OpenClaw's stored credentials and can cause confusing failures. Check with env | grep -i anthropic and unset any conflicting variables.
Resolving Environment Variable Conflicts
Environment variables are a common source of authentication confusion, especially for developers who previously used the Anthropic API directly before switching to OpenClaw. Variables set for direct API access can override OpenClaw's configuration, causing authentication to fail even with valid credentials stored.
The problematic variables are ANTHROPIC_API_KEY, ANTHROPIC_AUTH_TOKEN, ANTHROPIC_BASE_URL, and ANTHROPIC_API_URL. When set in your shell environment, these variables take precedence over values in OpenClaw's configuration files. The result is that OpenClaw uses credentials you didn't intend, or routes requests to the wrong endpoint.
To check for conflicting variables, run these commands:
bashenv | grep -i anthropic env | grep -i claude
If any variables appear, evaluate whether they should exist. For clean OpenClaw operation, you typically want these variables unset unless you're intentionally overriding the configuration.
To temporarily unset variables in your current shell:
bashunset ANTHROPIC_API_KEY unset ANTHROPIC_AUTH_TOKEN unset ANTHROPIC_BASE_URL
For permanent removal, edit your shell profile (.bashrc, .zshrc, or equivalent) and remove the export statements that set these variables. Then start a new shell session.
Docker deployments have an additional consideration: environment variables defined in docker-compose.yml or .env files override configuration. Check ~/.clawdbot/.env (the legacy location) and any compose file environment sections. Remove or correct any conflicting values there as well.
A clean environment check should show no Anthropic-related variables:
bashenv | grep -i anthropic
After clearing conflicting variables, restart your gateway and verify authentication works with openclaw models status.
Understanding the Cooldown Mechanism
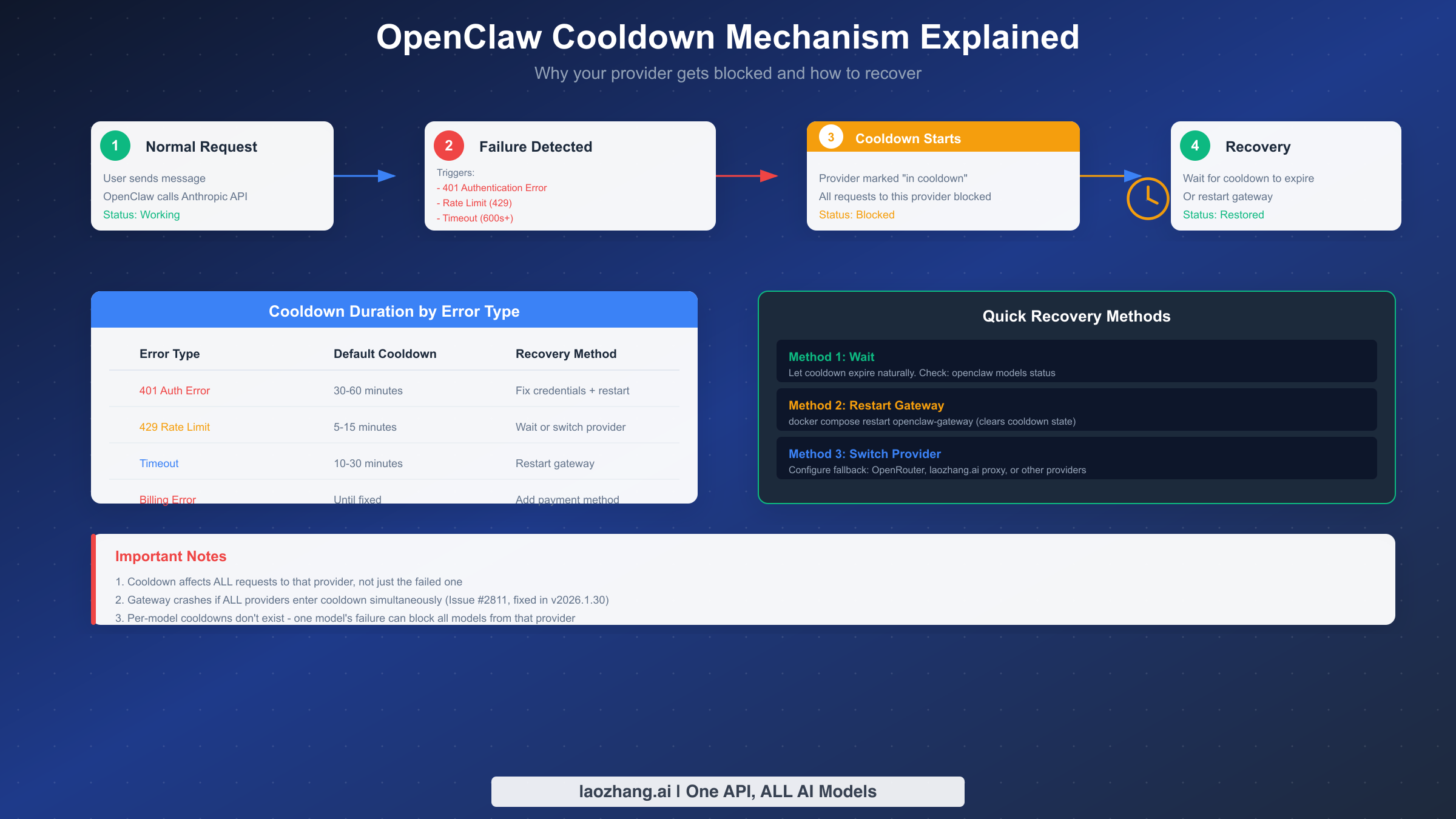
The cooldown mechanism is one of the most confusing aspects of OpenClaw authentication for new users. Your credentials can be perfectly valid, yet OpenClaw refuses to use them because the provider is "in cooldown." Understanding this mechanism helps you diagnose problems and recover quickly.
Cooldown is a protective feature that prevents cascading failures. When requests to a provider fail repeatedly, OpenClaw temporarily stops sending new requests to that provider. This prevents wasting time on requests that will fail, reduces API costs from failed calls, and gives the underlying issue time to resolve (such as temporary rate limits or network problems).
Several conditions trigger cooldown: authentication errors (401), rate limit errors (429), timeout errors (requests exceeding 600 seconds), and billing errors. Each failure type has different default cooldown durations. Authentication errors typically trigger longer cooldowns (30-60 minutes) because they indicate fundamental credential problems unlikely to resolve on their own. Rate limit cooldowns are shorter (5-15 minutes) because they represent temporary capacity issues.
The error message "No available auth profile for anthropic (all in cooldown)" indicates that all configured authentication profiles for Anthropic have entered cooldown state. This can happen with a single profile, or when multiple profiles all fail within a short time window.
To check cooldown status, run openclaw models status. The output shows each provider's current state, including cooldown remaining time if applicable. You'll see exactly how long until the provider becomes available again.
Recovery methods depend on your situation. The simplest approach is waiting for cooldown to expire naturally—the gateway automatically re-enables the provider when the cooldown period ends. For faster recovery, restart your gateway (docker compose restart openclaw-gateway), which clears the cooldown state. Note that restarting doesn't fix the underlying problem; if the credentials are invalid, you'll just trigger cooldown again.
A known issue (fixed in version 2026.1.30) caused the gateway to crash when all providers entered cooldown simultaneously. If you're on an older version and experiencing frequent gateway crashes, upgrading resolves this issue. The fix allows the gateway to wait gracefully for cooldown recovery rather than terminating.
For production deployments, configure multiple providers so that one provider's cooldown doesn't stop all AI functionality. OpenClaw supports automatic failover between providers—when Anthropic enters cooldown, it can fall back to OpenRouter, direct OpenAI access, or proxy services like laozhang.ai.
Choosing the Right Authentication Method
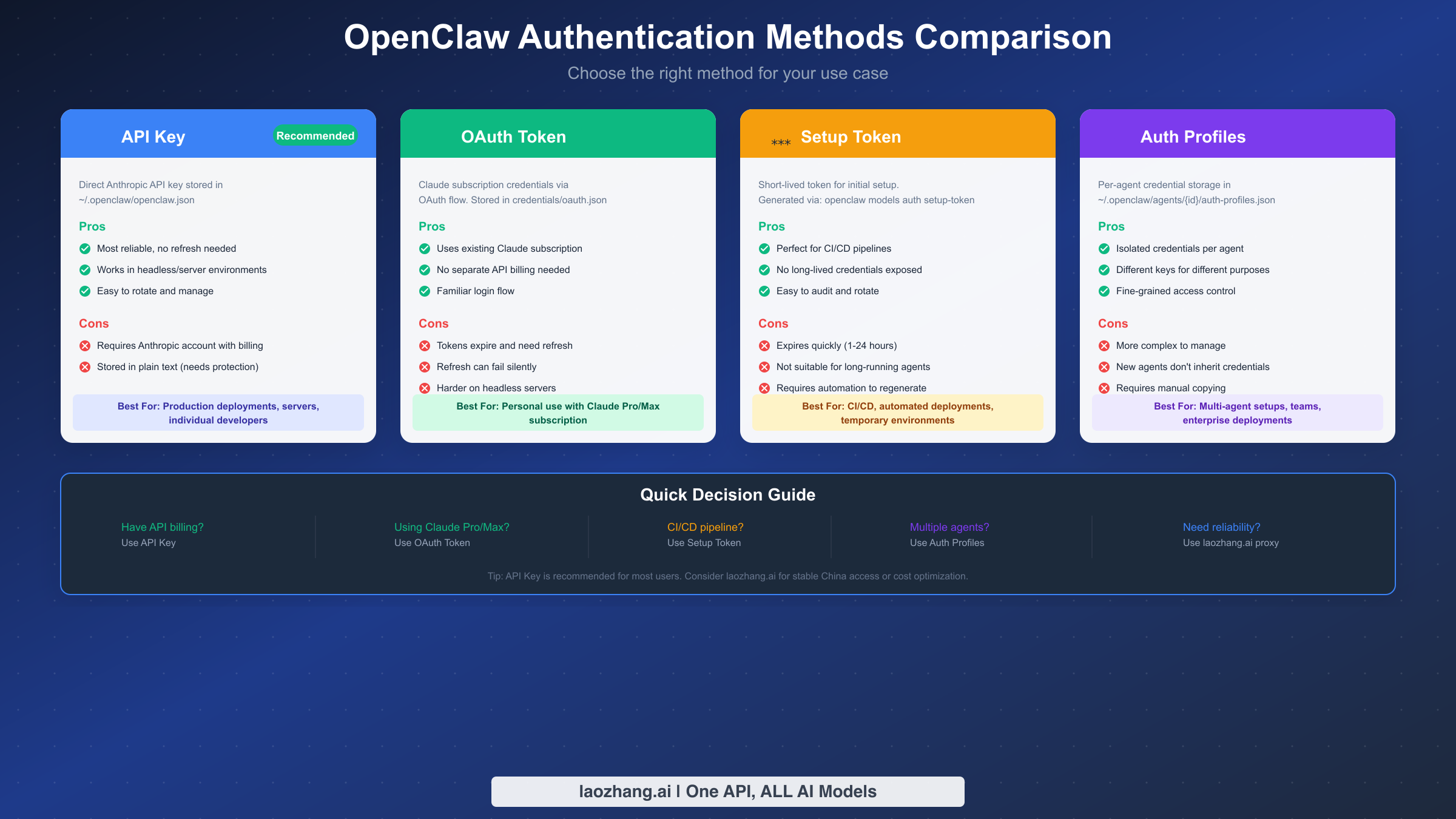
OpenClaw supports four authentication methods for Anthropic, each suited to different use cases. Choosing the right method from the start prevents many authentication headaches.
API Key is the recommended method for most users. You obtain a key from the Anthropic Console and store it in your configuration. Keys don't expire (unless you revoke them), work reliably in headless environments, and are easy to rotate. The downside is you need an Anthropic account with billing enabled, and the key is stored in plain text (requiring appropriate file permissions to protect it).
OAuth Token uses your Claude subscription credentials. This works well if you already have Claude Pro or Max and don't want separate API billing. However, tokens expire and need refresh, the refresh can fail silently, and headless server setups are more complicated because you need browser access for the OAuth flow.
Setup Token is designed for automated deployments. You generate a short-lived token (typically valid 1-24 hours) that's used only for initial configuration. This is perfect for CI/CD pipelines where you don't want long-lived credentials in your pipeline configuration. The token expires quickly, so it's not suitable for long-running agents that need to survive reboots.
Auth Profiles provide per-agent credential isolation. Each agent can have its own set of credentials stored in a separate file. This matters for teams where different agents should use different API accounts, or for enterprise deployments with billing separation. The complexity is that new agents don't inherit credentials—you must explicitly configure or copy credentials for each agent.
For individual developers running OpenClaw on a personal server, API Key is almost always the right choice. For users already paying for Claude Pro/Max who want to avoid separate API billing, OAuth works but requires understanding the refresh mechanism. For CI/CD and automated deployments, Setup Token provides the right security properties. For teams and enterprises, Auth Profiles offer the necessary isolation.
When choosing between Claude models for your OpenClaw deployment, consider that authentication method doesn't affect which models you can access—that's determined by your account tier and billing status.
Prevention and Maintenance
Preventing authentication errors is easier than troubleshooting them after they occur. A few maintenance practices keep your OpenClaw deployment running reliably.
Regular credential validation catches problems before they affect users. Add openclaw models status to your periodic health checks. The command takes seconds to run and immediately reveals any credential problems. For production deployments, consider automated monitoring that alerts when credentials become invalid.
Before updating OpenClaw, review the release notes for authentication-related changes. New versions occasionally modify default behavior or fix bugs that affect credentials. The upgrade itself won't overwrite your configuration files, but new defaults might interact differently with your existing setup.
Keep your credentials in one authoritative location. Multiple configuration sources (environment variables, config files, per-agent files) make troubleshooting difficult because you can't easily tell which source is active. Pick one method and use it consistently.
Backup your configuration regularly. The key files are ~/.openclaw/openclaw.json for main configuration, ~/.openclaw/credentials/oauth.json for OAuth tokens, and ~/.openclaw/agents/*/auth-profiles.json for per-agent credentials. Include these in your system backups.
For reliability across regions or during API outages, consider configuring a proxy service like laozhang.ai as a fallback provider. Proxy services can provide stable access when direct Anthropic API access is unreliable, and often offer cost advantages as well.
Document your authentication setup. Record which method you're using, why you chose it, and any special configuration. Future troubleshooting becomes much easier when you can reference what the setup should look like.
Frequently Asked Questions
Q: I applied a fix but still see authentication errors. What's wrong?
Multiple configuration sources can override each other. Run openclaw status --all to see your active configuration—it shows the effective values being used, not just what's in config files. Look for environment variables that might be overriding your configuration, or per-agent settings that differ from defaults.
Q: Why do I see "all in cooldown" when my credentials are correct?
Cooldown is triggered by past failures, not current credential validity. Even after fixing your credentials, existing cooldown continues until it expires. Restart your gateway to clear cooldown state immediately, or wait for the cooldown period to end.
Q: Can I use OAuth and API Key at the same time?
Yes, OpenClaw supports multiple auth profiles. You can configure both methods and use different ones for different agents. However, this adds complexity—for most users, picking one method and using it consistently is simpler.
Q: How do I know which authentication method I'm currently using?
Run openclaw configure --section auth to see your authentication configuration. The output shows which providers are configured and which authentication method each uses.
Q: My new agent doesn't have credentials even though my main agent works. Why?
Agents don't inherit credentials from other agents. Each agent has its own credential store in ~/.openclaw/agents/<agentId>/auth-profiles.json. You need to either run onboarding for the new agent or copy credentials from an existing agent's auth-profiles.json file.
The authentication landscape in OpenClaw can seem complex, but the fundamentals are straightforward: use the right credential type for your situation, keep credentials in one consistent location, and use the diagnostic commands when problems occur. Most authentication errors have simple fixes once you identify the specific issue.
![Fix OpenClaw Anthropic API Key Error: Complete Guide [2026]](/posts/en/openclaw-anthropic-api-key-error/img/cover.png)